
I hope you get value out of this blog post.
The data is clear:
According to a study by Sophos, 94% of cybersecurity and IT leaders across 14 countries encountered a cyberattack or security breach in 2022.
But there’s a looming concern we, as an industry, need to address head-on: The rapid advancement of AI's ability to create deepfakes.
Financial advisors, it's time for a crucial conversation about robust verification processes. This isn't just about adapting — it's about safeguarding our industry’s future.
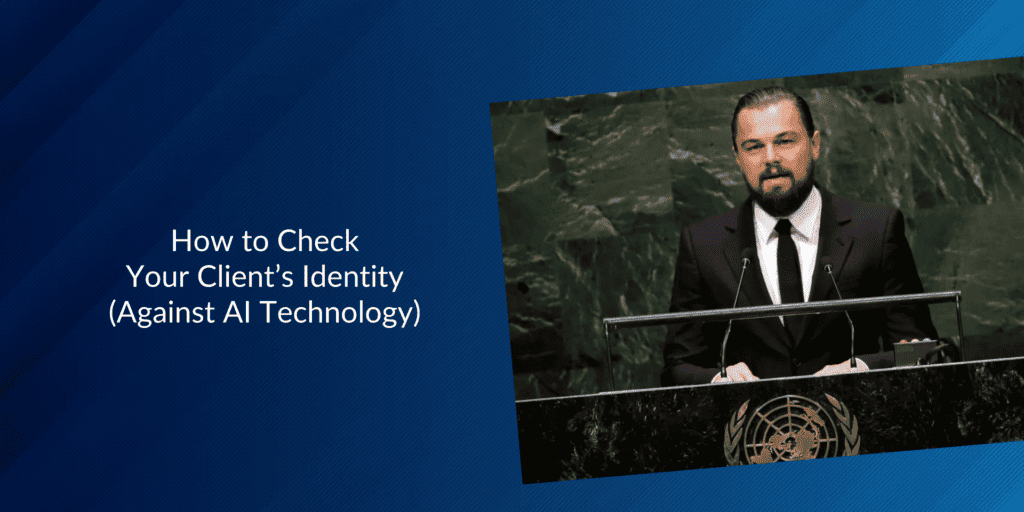
Before diving into the intricacies of the topic, take a moment to watch this video where Leonardo DiCaprio stands on stage.
But the voice (or voices) you would hear after a few seconds won’t be his:
They’re deepfake voices of various popular individuals created using Eleven Labs' AI voice cloning technology.
It's a stark reminder of the capabilities of AI and the potential dangers we face in a world where seeing and hearing might not always equate to believing.
Now imagine this:
You receive a call from a client instructing you to wire $50,000 to a specified account. The voice on the other end sounds exactly like your client, but how can you be sure?
With AI technology, voices can be mimicked to a tee — the same goes for video. Although live video is somewhat safer for now, the pace at which AI is advancing makes it a shaky reliance.
In the scenario painted, the risk of acting on a fraudulent request could result in significant financial loss and damage to your professional reputation.
The good news? There are several strategies and tools at your disposal to fortify the verification process.
We must consider a composite verification approach, integrating multiple methods to add layers of security.
This multi-faceted approach significantly minimizes the risks associated with fraudulent requests and unauthorized transactions.
Here’s a guide on how you can establish a composite verification framework:
Integrating a variety of verification methods enriches the security tapestry of your transaction processes:
Additionally, transaction safeguards such as OTP and PIN act as robust barriers to unauthorized transactions, ensuring that only authenticated requests are processed.
Tailoring the verification process to match the individual needs and technological adeptness of each client is crucial.
It's about striking a fine balance between maintaining high-security standards and providing a user-friendly experience.
Every client’s comfort level with technology and their preference for verification methods may vary.
This shows a level of understanding and a client-centric approach, which not only enhances the security but also enriches the client-advisor relationship.
The success of a mixed verification framework largely depends on how well your clients and staff know the different verification methods used.
It's important to teach your clients why each method matters and how they all work together to make transactions safe.
Similarly, regular training for your staff keeps them updated on any new methods. This helps them handle the verification process smoothly and securely.
It's crucial to have a mechanism in place for continuous monitoring of the verification framework to identify any weaknesses or areas for improvement.
Staying updated on emerging verification technologies and adapting your framework to address new challenges is essential.
In addition, gathering feedback from clients and staff can provide invaluable insights into how the verification process can be refined for better security and user experience.
Reverting to traditional verification methods may feel like taking a step back, yet, they offer a layer of simplicity and a personal touch in the verification process.
Sometimes, a touch of the old in our strategy can offer security and simplicity:
A secret word or phrase is a predetermined set of unique words shared between you and your client.
This arrangement adds a layer of security to your interactions, ensuring that the person you are communicating with is indeed your client.
The mechanism is straightforward:
Upon establishing a relationship with a client, you agree on a unique word or phrase that will be used in future communications to verify identity.
Whenever your client initiates a transaction request, they are required to provide this secret word or phrase. This acts as a verbal handshake, affirming their identity.
⚙️ How to implement:
⚠️ Note: If your client relationship system is compromised or hacked, alert your clients immediately and let them know that all previous transactions as well as verbal keys are off. You also need to meet with your clients as soon as possible to establish a new setup.
The premise is simple:
Whenever you receive a transaction request, especially one that seems unusual or comes through a less secure channel, you initiate a callback to your client using the contact information on file.
This step provides an additional layer of verification, ensuring the request is legitimate.
⚙️ How to implement:
Employing technological solutions not only modernizes your verification process but also adds layers of security that are tough for fraudsters to penetrate.
MFA is a security measure that requires users to provide two or more forms of identification before they can access a particular resource, like an account or a system.
This method is highly effective in reducing the risk of fraud, as it requires evidence from multiple categories of credentials.
Here’s how it works:
A user must successfully present credentials from at least two of these categories to gain access or complete a transaction.
⚙️ How to implement:
Biometric Verification is a security measure that uses unique biological or behavioral traits to verify an individual’s identity.
It's a reliable method of ensuring that the person you're interacting with is indeed your client, significantly minimizing the risks associated with AI-generated fraudulent requests.
Here’s how it works:
⚠️ Note: Voice recognition wouldn't work if we’re talking about AI that can copy voices (which may advance even further in the future).
The system captures and stores a digital representation of a person’s unique trait, which is then used for future verification.
⚙️ How to implement:
Biometric verification is a robust method for client authentication, but it may be best suited for larger firms with the means to implement and uphold it.
Smaller businesses should consider their operational needs and capabilities before adopting this technology.
You might already be doing this through Skype, Zoom, or a similar platform.
But secure video conferencing is a method that allows you to conduct face-to-face meetings with your clients, regardless of geographical distance.
Platforms use end-to-end encryption to protect the data transmitted during a video call, ensuring that only the intended recipients can view the information.
⚙️ How to implement:
By implementing secure video conferencing, you offer a human-centric, visually verifiable method of interaction, enhancing trust and communication security in your client relationships.
Fight fire with fire. 🔥
As AI technologies advance, they not only pose challenges but also provide solutions — AI-driven fraud detection is one such solution.
This innovative approach can be a game-changer in ensuring the authenticity of requests from clients, especially in the financial sector.
Here’s how it works:
⚙️ In terms of implementation:
It might be prudent to consult with established financial institutions such as Schwab or Fidelity or with your broker-dealer.
Understanding what technologies they're utilizing can provide a clearer picture of industry standards and best practices.
If direct implementation isn't feasible, it's essential to ask these institutions about their approach and how they're handling AI-driven fraud detection.
Employing AI-driven fraud detection enables a proactive approach towards identifying and thwarting fraudulent attempts.
This tech-savvy solution, when integrated with other verification methods, forms a robust defense against the sophisticated fraud attempts enabled by advancing AI technology.
In the financial sector, we need to set up safety nets:
Transaction limitations act as a financial safety net, ensuring that transactions above a certain threshold are flagged for additional verification.
How it works is that you and your client set a cap on the transaction amount that requires additional authentication for any transactions that exceed the predetermined limit.
This way, large transactions do not proceed without explicit approval, providing an opportunity to verify the client’s identity and the legitimacy of the request.
Naturally, this works well with secret words/phrases. You can establish another secret word/phrase for verifying large amounts or transactions.
⚙️ How to implement:
One-Time Passcodes add an extra layer of security by requiring a temporary code for transaction authorization.
How it works is that when a transaction is initiated, a unique, time-sensitive code is sent to the client via SMS or email.
The client must provide this code to proceed with the transaction, ensuring that only authorized individuals can complete transactions.
⚙️ How to implement:
Email confirmation is a simple yet effective measure to verify transactions
It provides an additional layer of security by requiring confirmation through a known email address before proceeding with a transaction.
Here’s how it works:
When a transaction is initiated, an email is sent to the client’s registered email address with the transaction details and a confirmation link or code.
The transaction will only proceed once the client confirms it via email.
⚙️ How to implement:
A Personal Identification Number (PIN) is a numerical code set by the client that serves as a secret identifier, adding a layer of security to transactions.
Clients set a unique PIN which is then required to authorize transactions. This additional step ensures that only authorized individuals can initiate or approve transactions.
⚙️ How to implement:
It's clear:
We, as an industry, need to be proactive, precise, and consistent. Financial advisors and professionals must adopt a proactive approach to counter these challenges.
By integrating traditional methods with cutting-edge technology, we can ensure a more secure and trustworthy financial environment for all stakeholders.
It’s evident that precision, consistency, and the right tools are paramount. Pulse360 stands out as a game-changer in this realm.
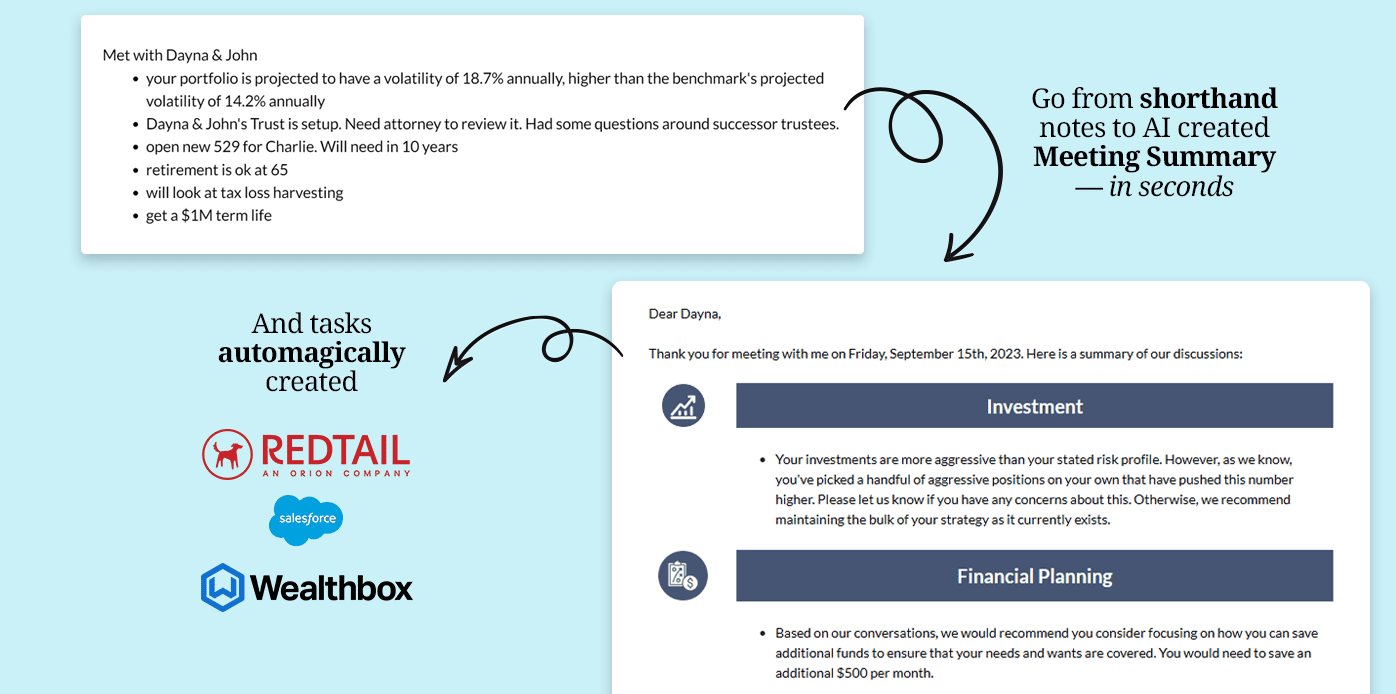
Consider the variety of plans tailored to every need:
In the evolving landscape of financial advisory, why remain stagnant? Streamline communications, document with ease, and capture every client nuance.
Dive into the future of financial advisory. Choose Pulse360 and witness the transformation.
